Petter Reinholdtsen: RAID status from LSI Megaraid controllers using free software
The last few days I have revisited RAID setup using the LSI
Megaraid controller. These are a family of controllers called PERC by
Dell, and is present in several old PowerEdge servers, and I recently
got my hands on one of these. I had forgotten how to handle this RAID
controller in Debian, so I had to take a peek in the
Debian wiki page
"Linux and Hardware RAID: an administrator's summary" to remember
what kind of software is available to configure and monitor the disks
and controller. I prefer Free Software alternatives to proprietary
tools, as the later tend to fall into disarray once the manufacturer
loose interest, and often do not work with newer Linux Distributions.
Sadly there is no free software tool to configure the RAID setup, only
to monitor it. RAID can provide improved reliability and resilience in
a storage solution, but only if it is being regularly checked and any
broken disks are being replaced in time. I thus want to ensure some
automatic monitoring is available.
In the discovery process, I came across a old free software tool to
monitor PERC2, PERC3, PERC4 and PERC5 controllers, which to my
surprise is not present in debian. To help change that I created a
request for packaging of the
megactl package, and tried to track down a usable version.
The original project
site is on Sourceforge, but as far as I can tell that project has
been dead for more than 15 years. I managed to find a
more recent fork on
github from user hmage, but it is unclear to me if this is still
being maintained. It has not seen much improvements since 2016. A
more up to date
edition is a git fork from the original github fork by user
namiltd, and this newer fork seem a lot more promising. The owner of
this github repository has replied to change proposals within hours,
and had already added some improvements and support for more hardware.
Sadly he is reluctant to commit to maintaining the tool and stated in
my first pull
request that he think a new release should be made based on the
git repository owned by hmage. I perfectly understand this
reluctance, as I feel the same about maintaining yet another package
in Debian when I barely have time to take care of the ones I already
maintain, but do not really have high hopes that hmage will have time
to spend on it and hope namiltd will change his mind.
In any case, I created
a draft package
based on the namiltd edition and put it under the debian group on
salsa.debian.org. If you own a Dell PowerEdge server with one of the
PERC controllers, or any other RAID controller using the megaraid or
megaraid_sas Linux kernel modules, you might want to check it out. If
enough people are interested, perhaps the package will make it into
the Debian archive.
There are two tools provided, megactl for the megaraid Linux kernel
module, and megasasctl for the megaraid_sas Linux kernel module. The
simple output from the command on one of my machines look like this
(yes, I know some of the disks have problems. :).
# megasasctl a0 PERC H730 Mini encl:1 ldrv:2 batt:good a0d0 558GiB RAID 1 1x2 optimal a0d1 3067GiB RAID 0 1x11 optimal a0e32s0 558GiB a0d0 online errs: media:0 other:19 a0e32s1 279GiB a0d1 online a0e32s2 279GiB a0d1 online a0e32s3 279GiB a0d1 online a0e32s4 279GiB a0d1 online a0e32s5 279GiB a0d1 online a0e32s6 279GiB a0d1 online a0e32s8 558GiB a0d0 online errs: media:0 other:17 a0e32s9 279GiB a0d1 online a0e32s10 279GiB a0d1 online a0e32s11 279GiB a0d1 online a0e32s12 279GiB a0d1 online a0e32s13 279GiB a0d1 online #In addition to displaying a simple status report, it can also test individual drives and print the various event logs. Perhaps you too find it useful? In the packaging process I provided some patches upstream to improve installation and ensure a Appstream metainfo file is provided to list all supported HW, to allow isenkram to propose the package on all servers with a relevant PCI card. As usual, if you use Bitcoin and want to show your support of my activities, please send Bitcoin donations to my address 15oWEoG9dUPovwmUL9KWAnYRtNJEkP1u1b.
 Mee Goreng, a dish made of noodles in Malaysia.
Mee Goreng, a dish made of noodles in Malaysia.
 Me at Petronas Towers.
Me at Petronas Towers.
 Photo with Malaysians.
Photo with Malaysians.
 Update 28.02.2024 19:45 CET: There is now a blog entry at
Update 28.02.2024 19:45 CET: There is now a blog entry at  The blog post you re reading is hosted on a private Kubernetes cluster that runs inside my home. Another workload that s running on same cluster is...
The post
The blog post you re reading is hosted on a private Kubernetes cluster that runs inside my home. Another workload that s running on same cluster is...
The post  We have a cabin out in the forest, and when I say "out in the forest" I mean "in a national forest subject to regulation by the US Forest Service" which means there's an extremely thick book describing the things we're allowed to do and (somewhat longer) not allowed to do. It's also down in the bottom of a valley surrounded by tall trees (the whole "forest" bit). There used to be AT&T copper but all that infrastructure burned down in a big fire back in 2021 and AT&T no longer supply new copper links, and Starlink isn't viable because of the whole "bottom of a valley surrounded by tall trees" thing along with regulations that prohibit us from putting up a big pole with a dish on top. Thankfully there's LTE towers nearby, so I'm simply using cellular data. Unfortunately my provider rate limits connections to video streaming services in order to push them down to roughly SD resolution. The easy workaround is just to VPN back to somewhere else, which in my case is just a Wireguard link back to San Francisco.
We have a cabin out in the forest, and when I say "out in the forest" I mean "in a national forest subject to regulation by the US Forest Service" which means there's an extremely thick book describing the things we're allowed to do and (somewhat longer) not allowed to do. It's also down in the bottom of a valley surrounded by tall trees (the whole "forest" bit). There used to be AT&T copper but all that infrastructure burned down in a big fire back in 2021 and AT&T no longer supply new copper links, and Starlink isn't viable because of the whole "bottom of a valley surrounded by tall trees" thing along with regulations that prohibit us from putting up a big pole with a dish on top. Thankfully there's LTE towers nearby, so I'm simply using cellular data. Unfortunately my provider rate limits connections to video streaming services in order to push them down to roughly SD resolution. The easy workaround is just to VPN back to somewhere else, which in my case is just a Wireguard link back to San Francisco. Just like the corset, I also needed a new pair of jeans.
Back when my body size changed drastically of course my jeans no longer
fit. While I was waiting for my size to stabilize I kept wearing them
with a somewhat tight belt, but it was ugly and somewhat uncomfortable.
When I had stopped changing a lot I tried to buy new ones in the same
model, and found out that I was too thin for the menswear jeans of that
shop. I could have gone back to wearing women s jeans, but I didn t want
to have to deal with the crappy fabric and short pockets, so I basically
spent a few years wearing mostly skirts, and oversized jeans when I
really needed trousers.
Meanwhile, I had drafted a
Just like the corset, I also needed a new pair of jeans.
Back when my body size changed drastically of course my jeans no longer
fit. While I was waiting for my size to stabilize I kept wearing them
with a somewhat tight belt, but it was ugly and somewhat uncomfortable.
When I had stopped changing a lot I tried to buy new ones in the same
model, and found out that I was too thin for the menswear jeans of that
shop. I could have gone back to wearing women s jeans, but I didn t want
to have to deal with the crappy fabric and short pockets, so I basically
spent a few years wearing mostly skirts, and oversized jeans when I
really needed trousers.
Meanwhile, I had drafted a  Making also went smoothly, and the result was fitting. Very fitting. A
big too fitting, and the standard bum adjustment of the back was just
enough for what apparently still qualifies as a big bum, so I adjusted
the pattern to be able to add a custom amount of ease in a few places.
But at least I had a pair of jeans-shaped trousers that fit!
Except, at 200 g/m I can t say that fabric is the proper weight for a
pair of trousers, and I may have looked around online
Making also went smoothly, and the result was fitting. Very fitting. A
big too fitting, and the standard bum adjustment of the back was just
enough for what apparently still qualifies as a big bum, so I adjusted
the pattern to be able to add a custom amount of ease in a few places.
But at least I had a pair of jeans-shaped trousers that fit!
Except, at 200 g/m I can t say that fabric is the proper weight for a
pair of trousers, and I may have looked around online In October 2023, I departed from the
In October 2023, I departed from the  In light of the recent
In light of the recent 
 Like each month, have a look at the work funded by
Like each month, have a look at the work funded by 






 New Year, Same Great People! Our Debian User Group met for the first of our
2024 bi-monthly meetings on February 4th and it was loads of fun. Around
twelve different people made it this time to
New Year, Same Great People! Our Debian User Group met for the first of our
2024 bi-monthly meetings on February 4th and it was loads of fun. Around
twelve different people made it this time to 


 Inspired by a
Inspired by a 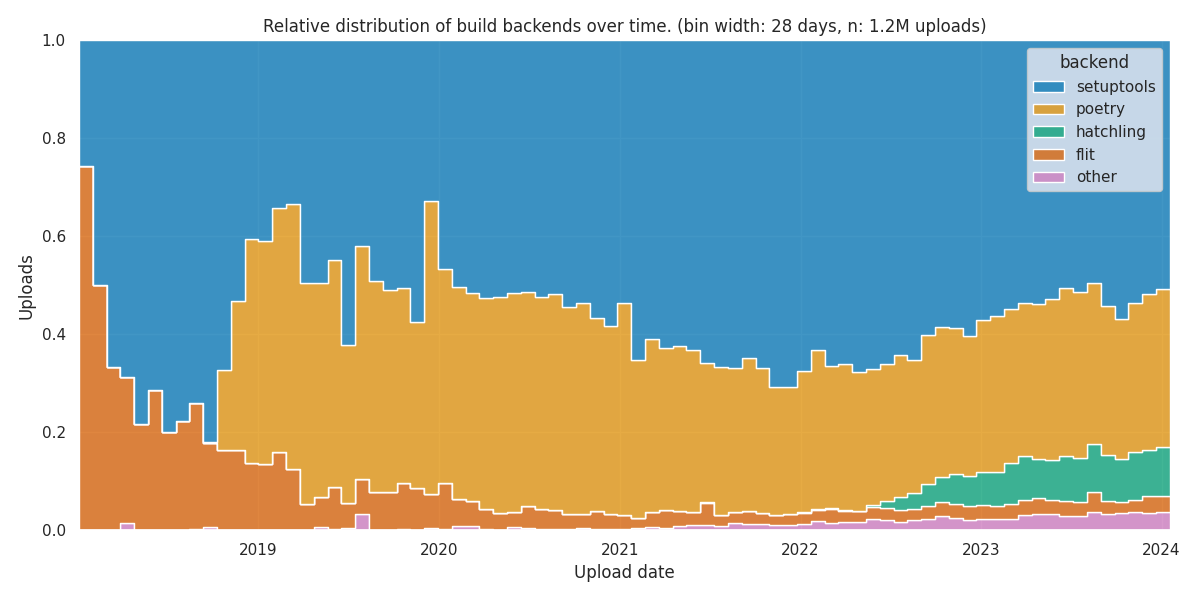
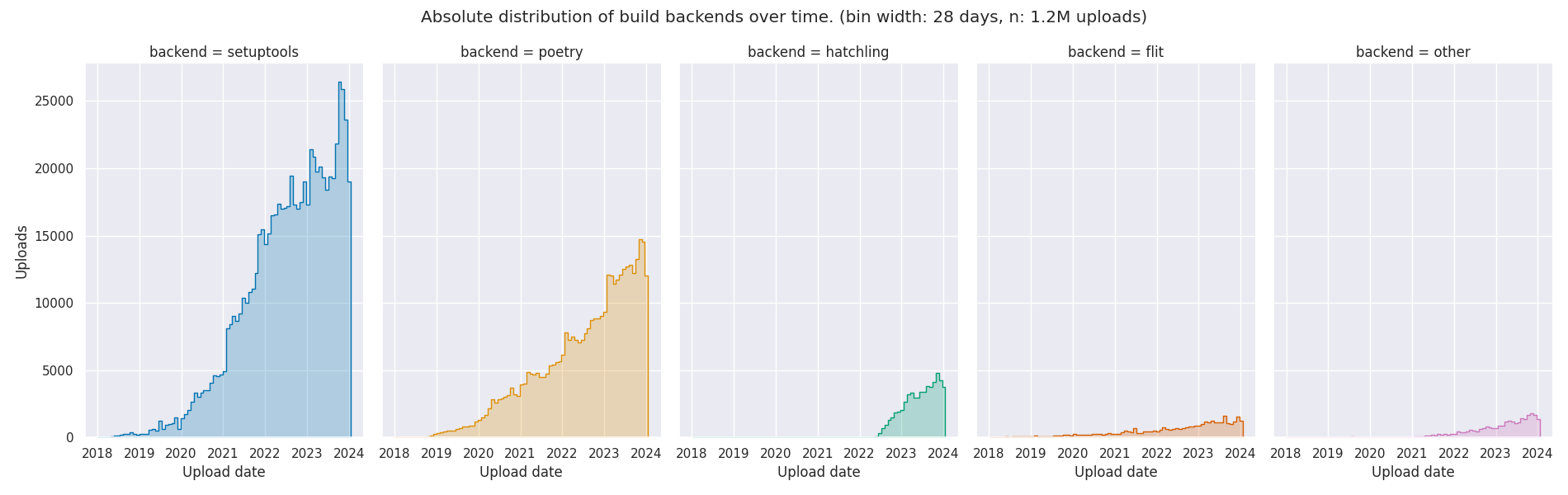

 The
The